Simple Certificate Enrollment Protocol
As a Service

Protect your Organization’s Data and Ensure High Levels of Secure Authentication
What is a SCEP Server?
A SCEP (Simple Certificate Enrollment Protocol) server is a server that is used to issue digital certificates to devices on a network. SCEP is a protocol that is used to automate the process of enrolling and issuing digital certificates, which are used to authenticate devices and users on a network.
A SCEP server typically works in conjunction with a Public Key Infrastructure (PKI) to issue and manage digital certificates. The SCEP server is responsible for receiving certificate enrollment requests from devices on the network, verifying the identity of the device, and then issuing a digital certificate that can be used to authenticate the device on the network.
In order to enroll for a certificate, a device will typically request a Certificate Signing Request (CSR) from the SCEP server, which is then used to generate a digital certificate. The certificate can be used to authenticate the device to other devices and services on the network.
SCEP is commonly used in enterprise environments to issue digital certificates to devices such as smartphones, tablets, laptops, and other network-connected devices. By using digital certificates, administrators can authenticate devices and ensure that only authorized devices are allowed to access the network. This helps to improve network security and reduce the risk of unauthorized access and data breaches.
Overall, a SCEP server is an important component of a PKI infrastructure, providing an automated way to issue digital certificates and ensure the security of network-connected devices.
What Type of Businesses Use SCEP Servers?
Any business that has a need for secure network communication and authentication can use a SCEP (Simple Certificate Enrollment Protocol) server. In particular, businesses that have a large number of network-connected devices, such as smartphones, tablets, laptops, and other Internet of Things (IoT) devices, can benefit from using a SCEP server to issue digital certificates.
Here are some examples of businesses that can benefit from using a SCEP server:
-
Healthcare organizations: Healthcare organizations must comply with strict security regulations to protect sensitive patient data. A SCEP server can be used to issue digital certificates to medical devices and staff devices to ensure secure network communication and access control.
-
Financial institutions: Banks, credit unions, and other financial institutions handle sensitive financial information that must be kept secure. A SCEP server can be used to issue digital certificates to devices used by employees and customers to ensure secure communication and prevent unauthorized access.
-
Education institutions: Schools and universities have a large number of devices and users that require secure network access. A SCEP server can be used to issue digital certificates to devices such as student laptops and tablets, as well as faculty and staff devices.
-
Manufacturing companies: Manufacturing companies may use a variety of IoT devices, such as sensors and robotics, that require secure network communication. A SCEP server can be used to issue digital certificates to these devices to ensure secure communication and prevent unauthorized access.
-
Government agencies: Government agencies have strict security requirements to protect sensitive data and prevent cyberattacks. A SCEP server can be used to issue digital certificates to government devices and systems to ensure secure communication and access control.
Overall, any business that has a need for secure network communication and authentication can benefit from using a SCEP server to issue digital certificates. By ensuring secure communication and access control, businesses can protect sensitive data, prevent unauthorized access, and improve network security.
How Can IronWiFi's SCEP Servers Help Your Business?
IronWiFi's SCEP (Simple Certificate Enrollment Protocol) servers can help a business in several ways:
-
Enhanced network security: Using passwordless certificate-based authentication on your network enhances your organisation's overall security. Digital certificates provide a way to authenticate devices and users on the network, ensuring that only authorized devices and users are allowed access. SCEP server simplifies the process of distributing those certificates.
-
Simplified certificate management: IronWiFi's SCEP servers can simplify the process of managing digital certificates. The SCEP server can automate the process of enrolling and issuing certificates, reducing the workload on IT staff and ensuring that certificates are issued and managed consistently.
-
Improved compliance: Many industries have regulations that require the use of digital certificates for secure network communication. By using IronWiFi's SCEP servers to issue digital certificates, businesses can ensure compliance with these regulations.
-
Increased efficiency: IronWiFi's SCEP servers can automate the process of issuing and managing digital certificates, reducing the workload on IT staff and freeing them up to focus on other tasks.
-
Flexibility: IronWiFi's SCEP servers can be used with a variety of devices and platforms, making them a flexible solution for businesses that have a diverse range of network-connected devices.
Overall, IronWiFi's SCEP servers can help a business to enhance its network security, simplify certificate management, improve compliance, increase efficiency, and provide flexibility for managing a diverse range of network-connected devices.
Why SCEP?
SCEP (Simple Certificate Enrollment Protocol) is a widely used protocol for issuing digital certificates to devices on a network. Here are some factors that make SCEP a popular and effective choice for businesses:
-
Ease of use: SCEP is a straightforward protocol that can be easily integrated into existing network infrastructure. It can be used with a wide range of devices and platforms, making it a flexible solution for businesses.
-
Automation: SCEP allows for the automation of the certificate enrollment process, which can save time and reduce the workload on IT staff. This can be particularly beneficial for businesses that have a large number of devices on their network.
-
Security: SCEP uses standard cryptographic protocols to secure the certificate enrollment and issuance process. This ensures that the certificates are issued securely and cannot be compromised.
-
Cost-effective: SCEP is a cost-effective solution for issuing digital certificates. It can be used with a wide range of devices, reducing the need for businesses to purchase expensive proprietary solutions.
-
Widely adopted: SCEP is a widely adopted protocol that is supported by many vendors and platforms. This makes it a safe and reliable choice for businesses that want to ensure compatibility with a range of devices and platforms.
Overall, SCEP is a popular and effective choice for businesses that need to issue digital certificates to devices on their network. It is easy to use, secure, cost-effective, and widely adopted, making it a flexible solution that can meet the needs of a wide range of businesses.
Access a Simple and Lightweight Protocol for Maximum Security

Easy issuance of device and user certificates. Simple configuration of certificates on diverse devices.

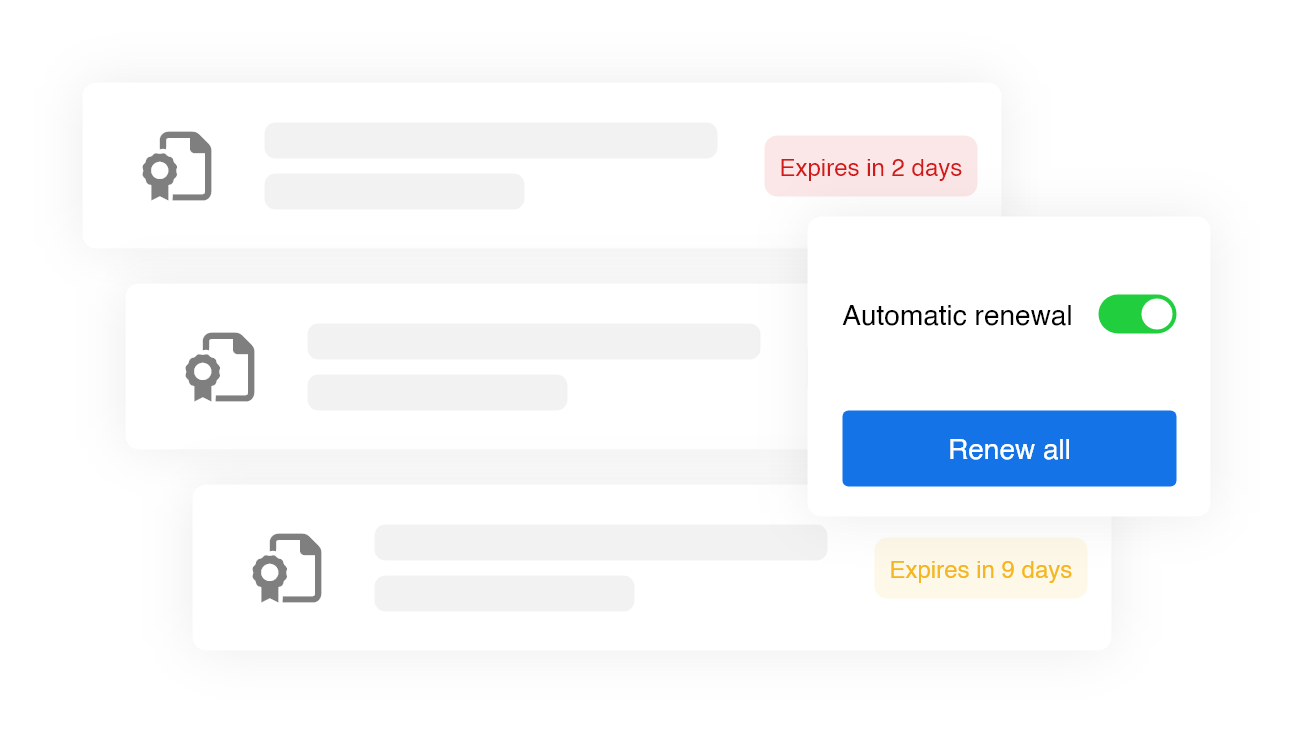
Certificates are issued and renewed automatically with little to no human involvement.

The protocol allows IT administrators to focus on the other tasks while simultaneously reducing operating costs and indirectly improving productivity

With SCEP you can manage devices running the most popular operating systems including Microsoft Windows, Apple iOS, macOS, Linux, and directory systems like Active Directory.
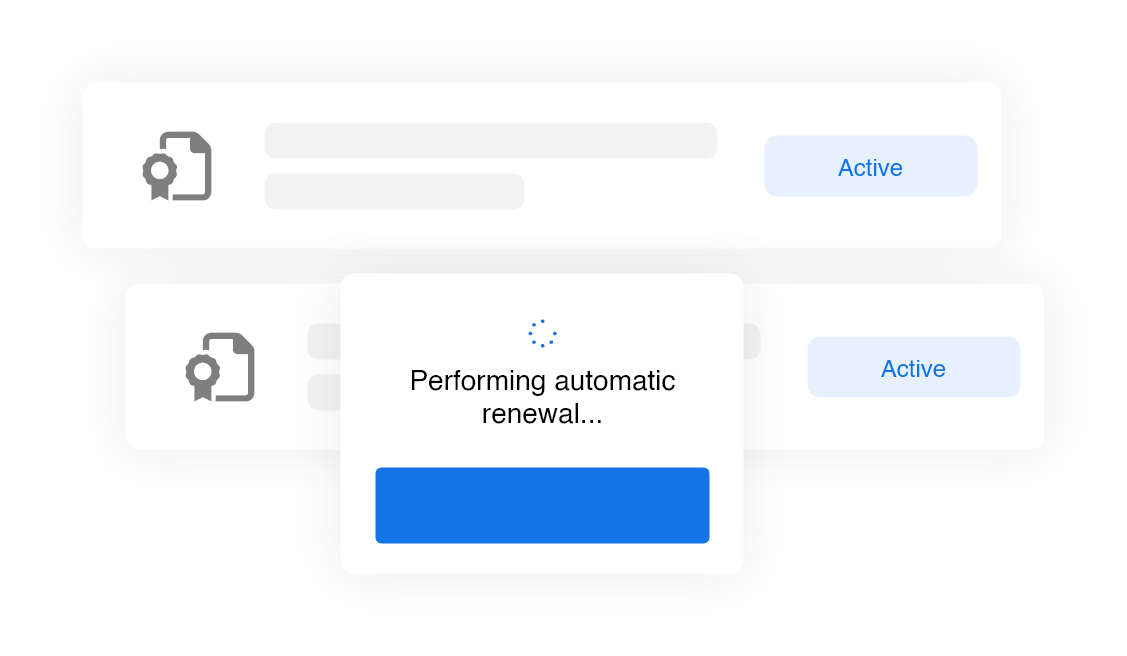
Easy Issuance
Issue device and user certificates in an easy and seamless way. Integrate a Public Key Infrastructure (PKI), configure gateways, set up policies, enroll certificates and authorize devices one time for permanent use.
The IronWiFi platform is based on open standards and provides enterprise-level quality of service, data protection, and security. The solution is 100% cloud-based with components provided directly by the hosting provider as a service. The solution supports more than 45 different vendors and has 50+ integrations.
