Azure Active Directory connector setup
To manage your wireless users using Azure Active Directory account, you can enable remote synchronization with your Azure account for users in specific groups.
- Log in to the Azure Portal
- From the main menu, navigate to Azure Active Directory > Properties > Tenant ID Copy the Tenant ID value.
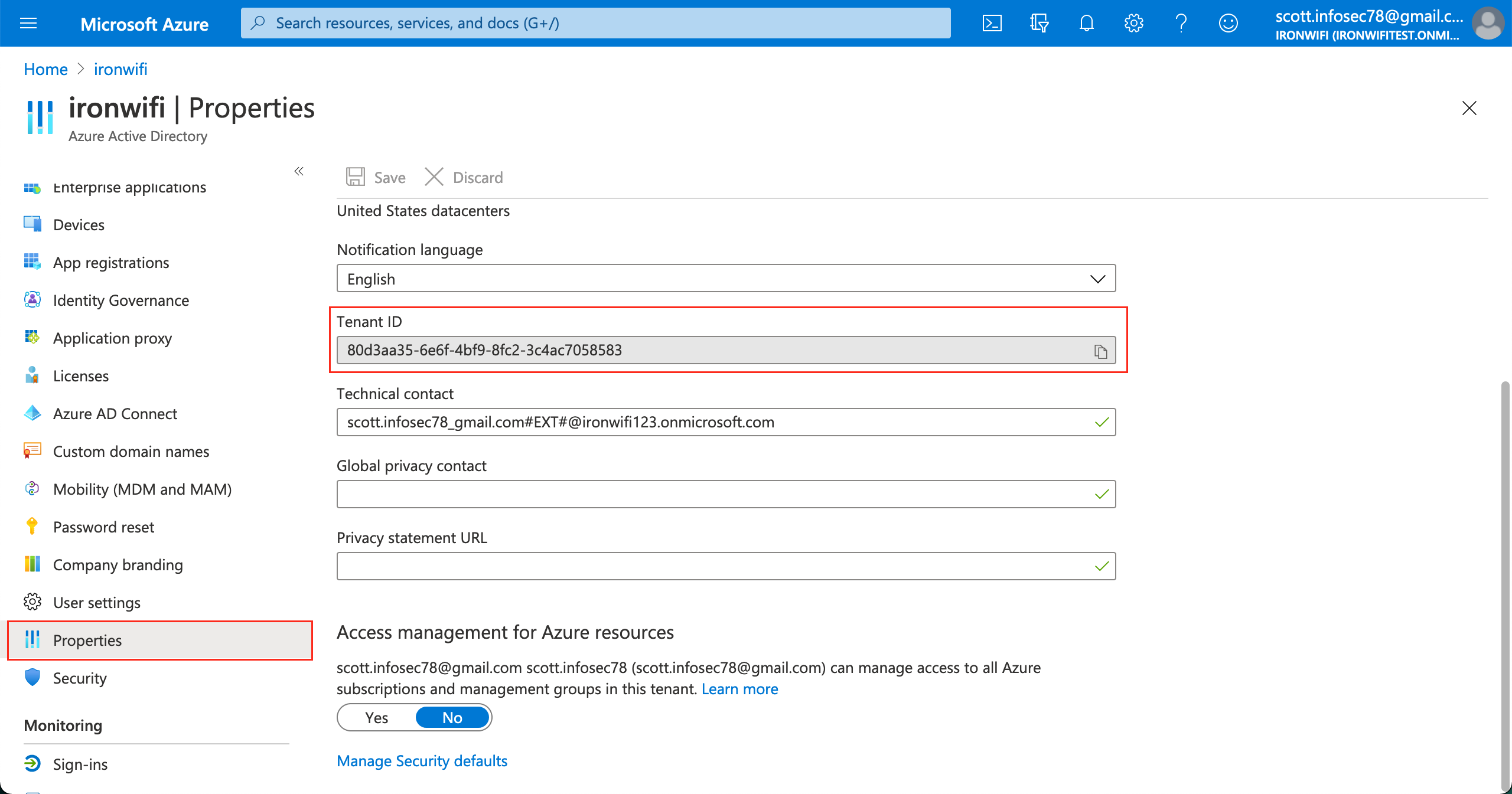
3. From the menu, go to Azure Active Directory -> App registrations
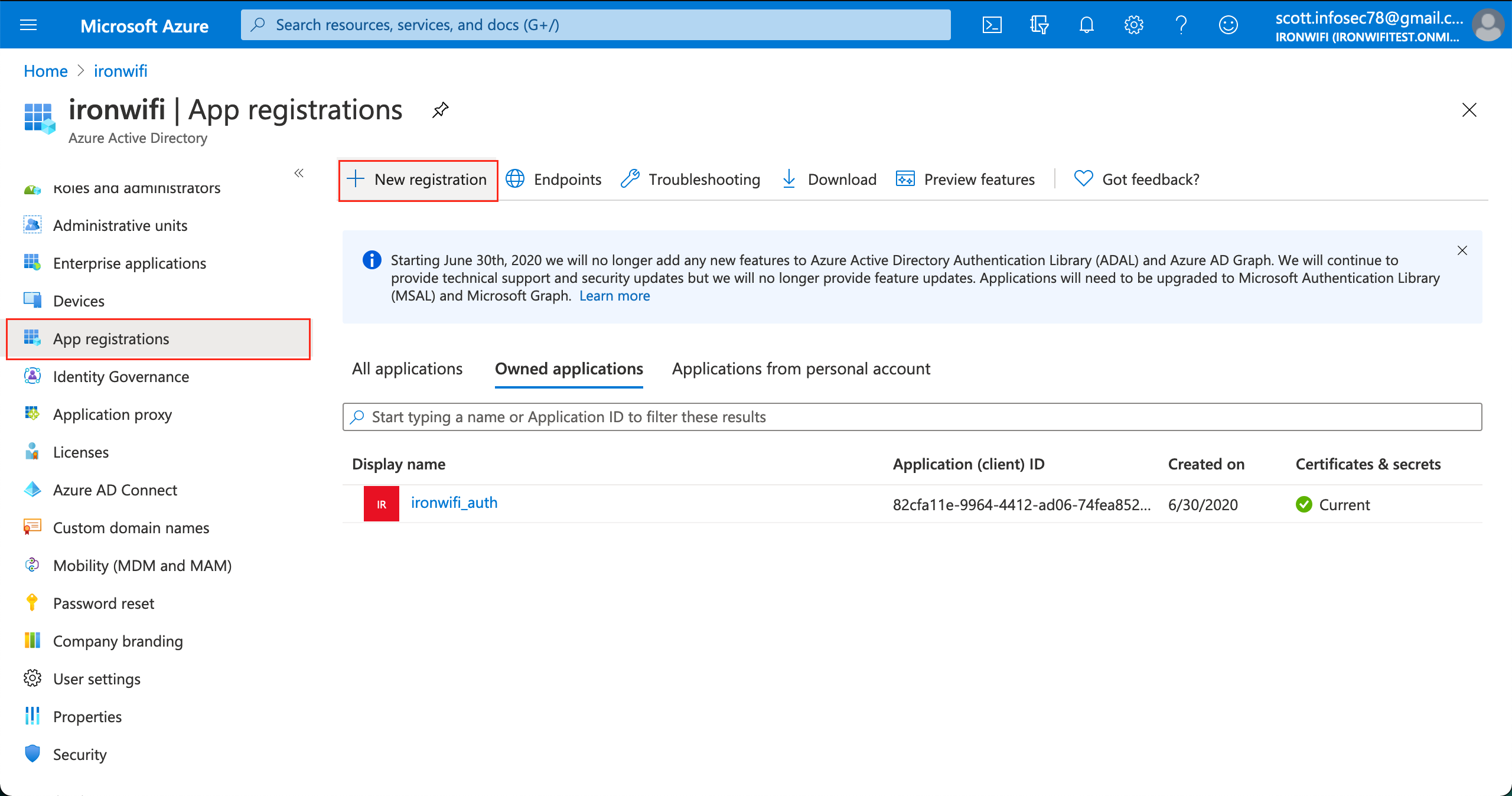
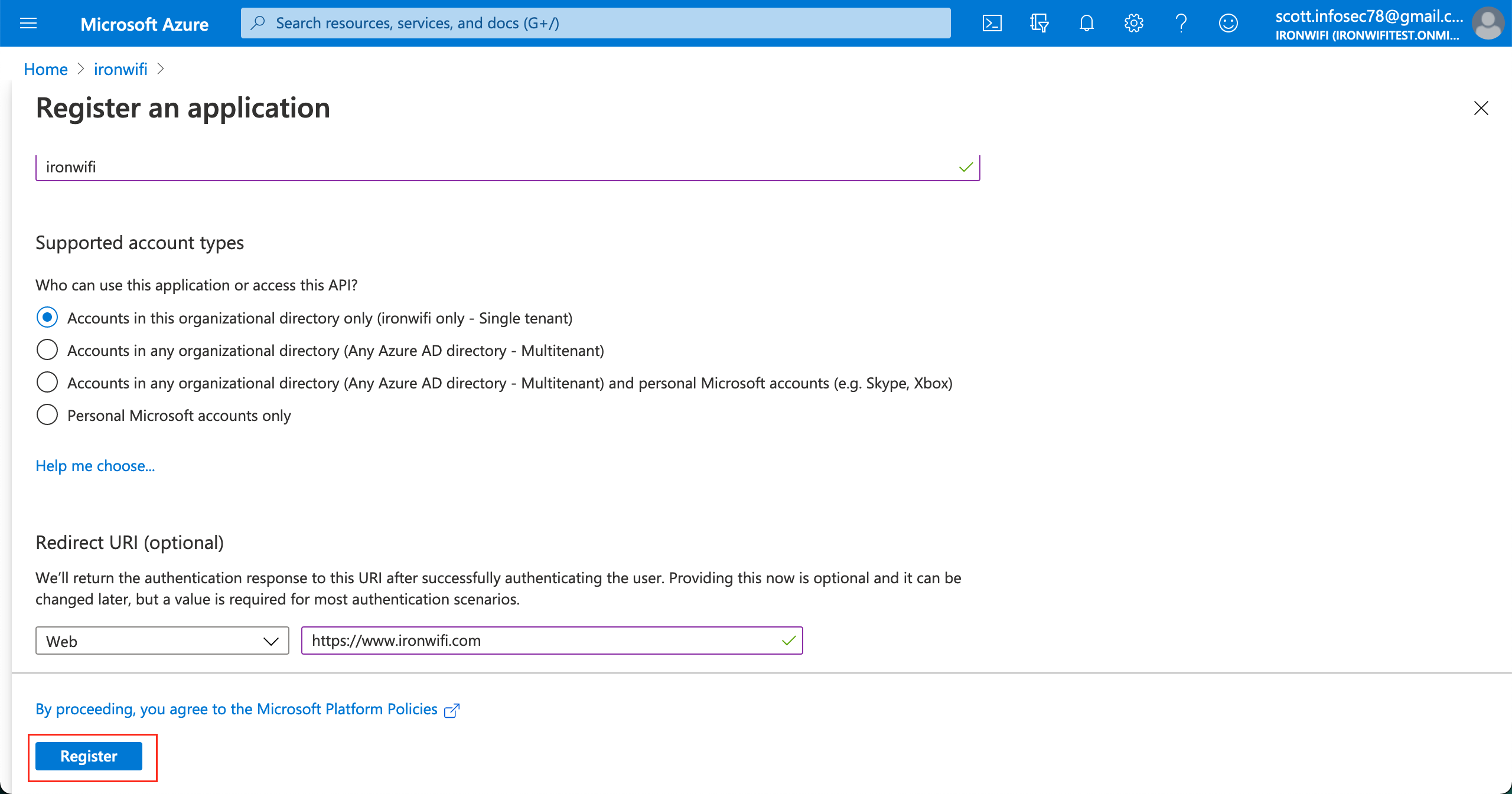
4. Click on New application registration 1. Name - ironwifi for example 2. Application type - Web app / API 3. Sign-on URL - https://www.ironwifi.com
5. Copy the Application ID value.
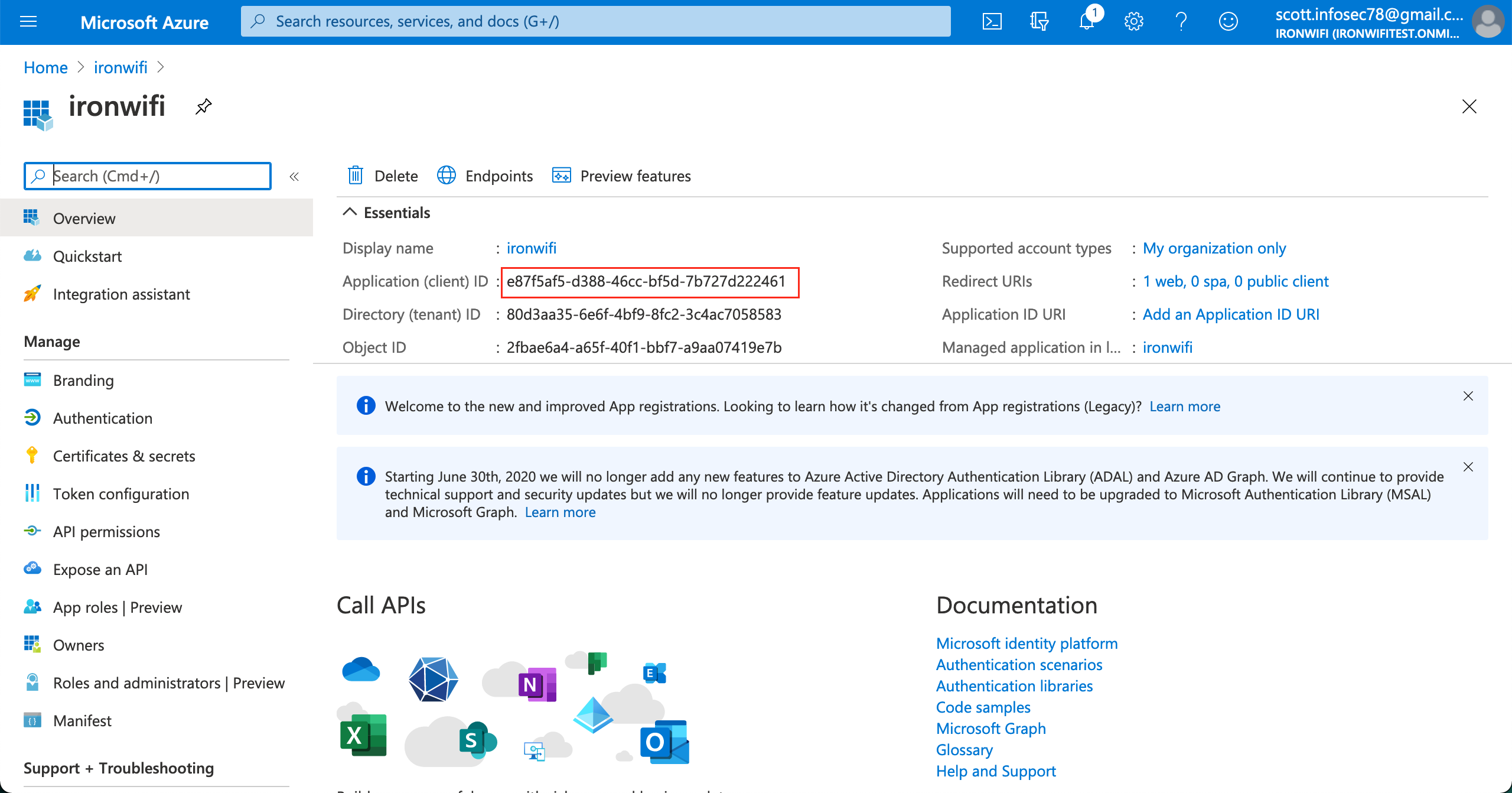
6. Click on the link next to Redirect URIs button.
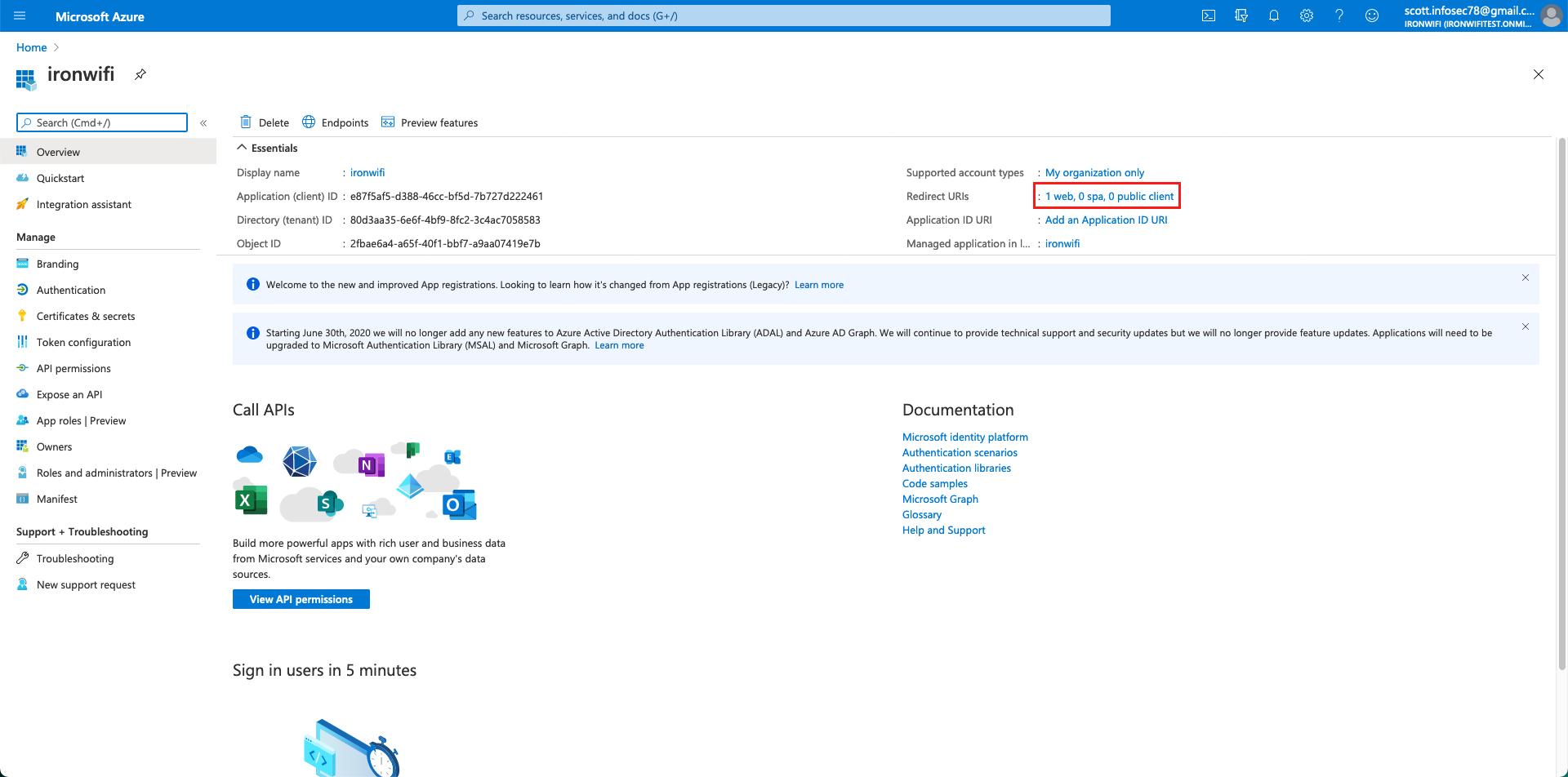
7. Under Redirect URIs, click add and paste this link https://console.ironwifi.com/api/oauth2callback. If you are using some other region, replace console with the territory, e.g., us-west1.ironwifi.com. Don't forget to hit save.
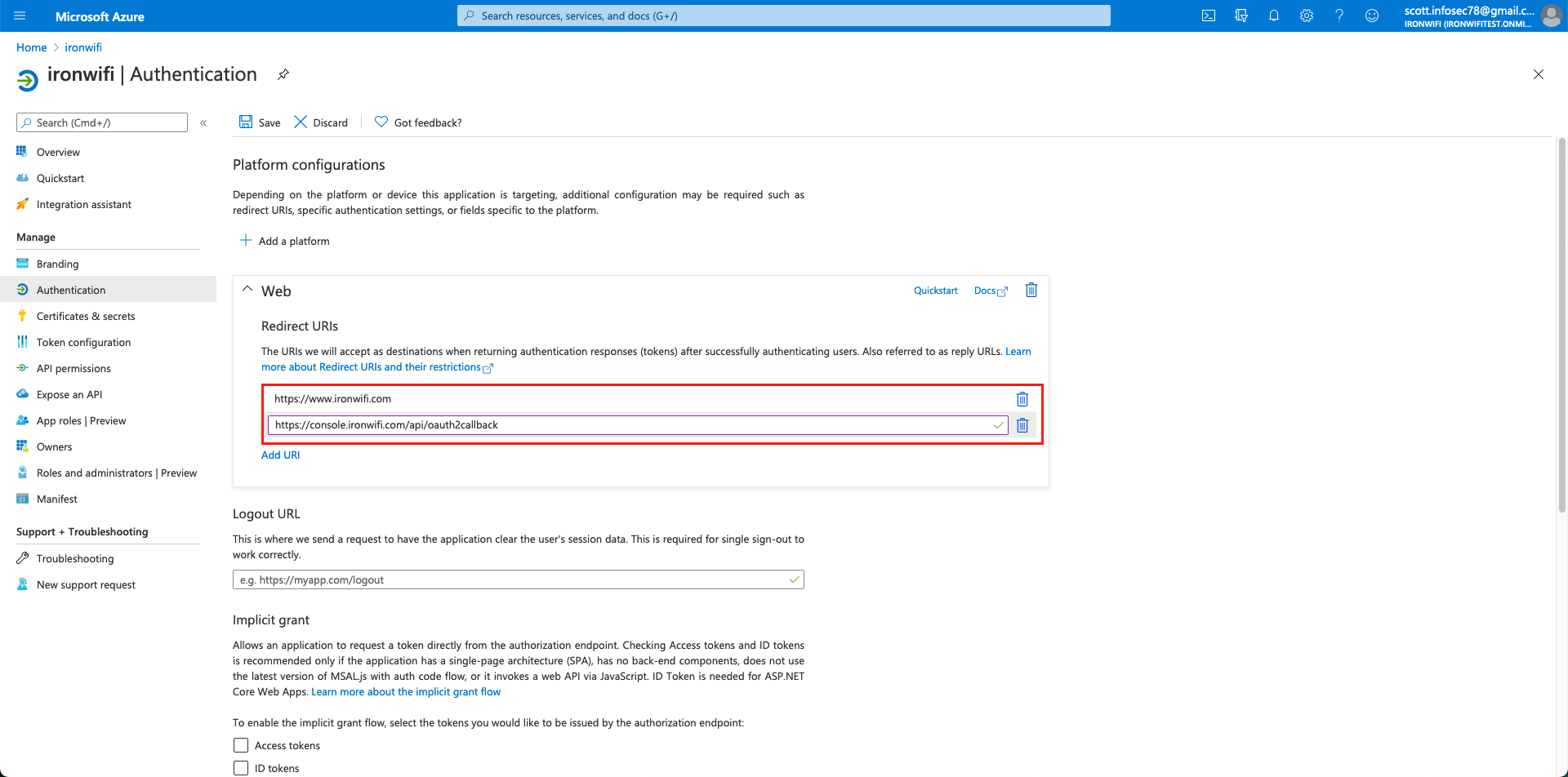
8. Click on API permissions in the left menu and click Add Permission
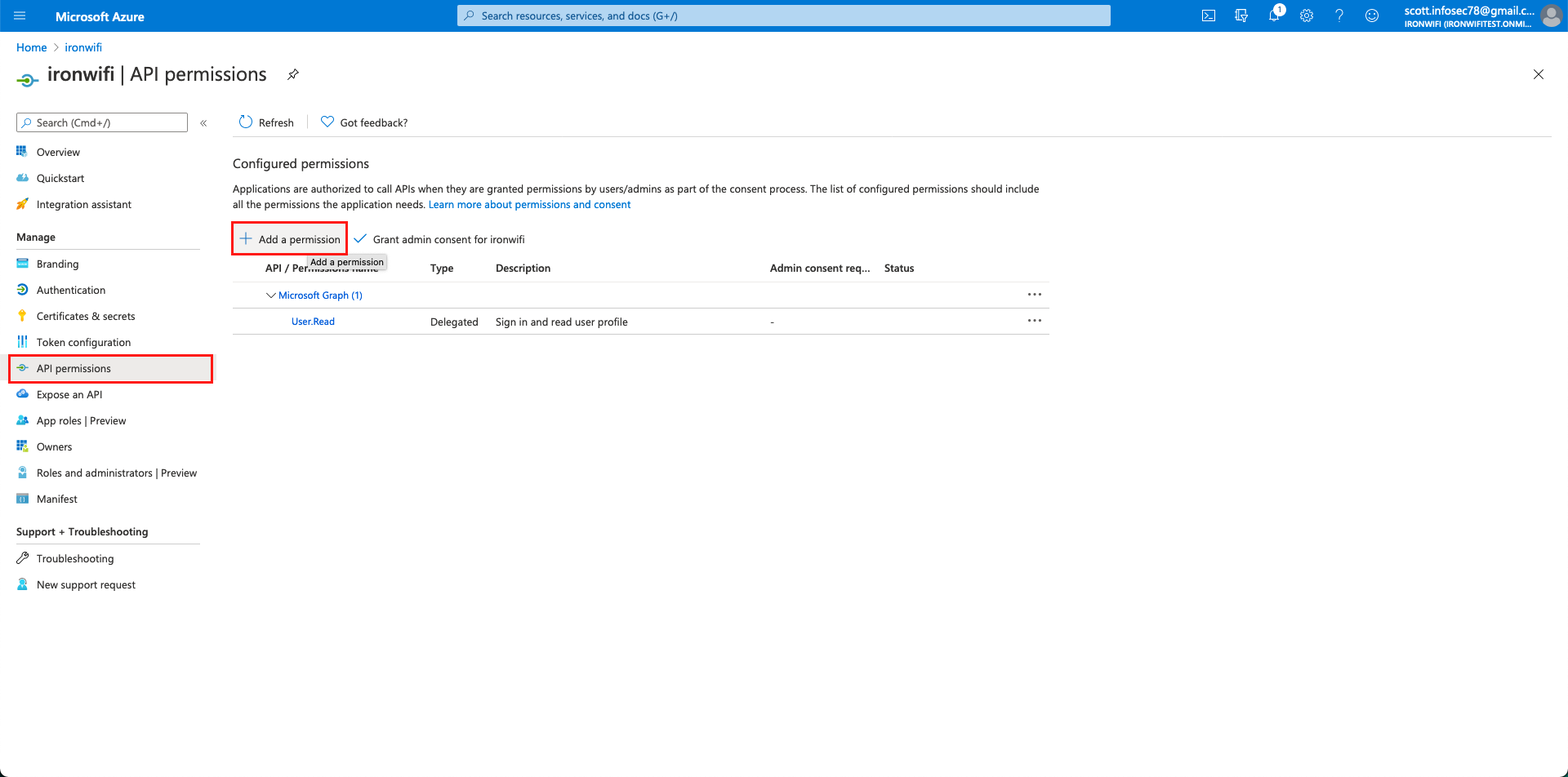
9. Click on Microsoft Graph -> Application Permissions and scroll down for Directory → Directory.Read.All. Click on Grant admin consent for the application (ironwifi)
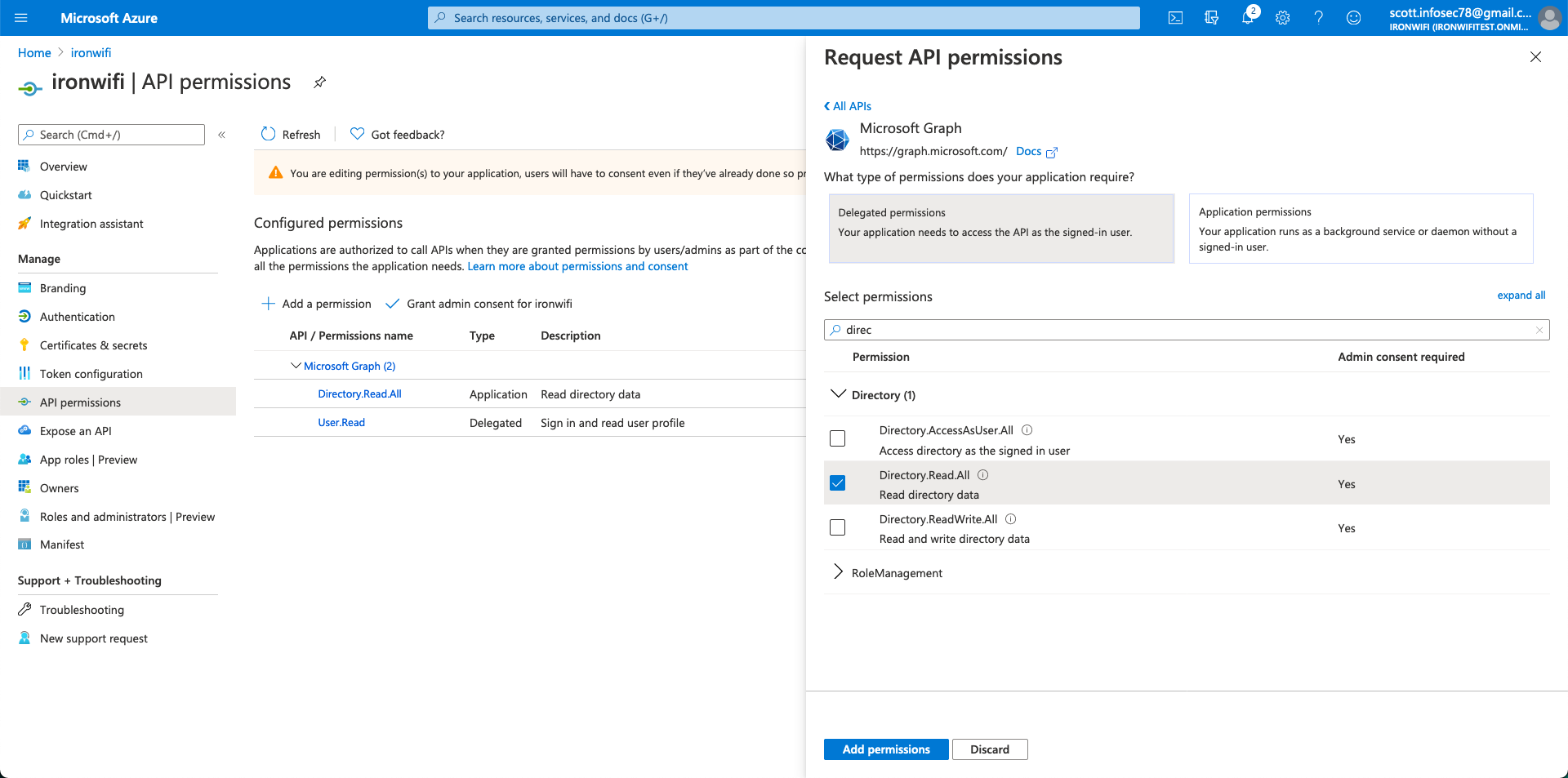
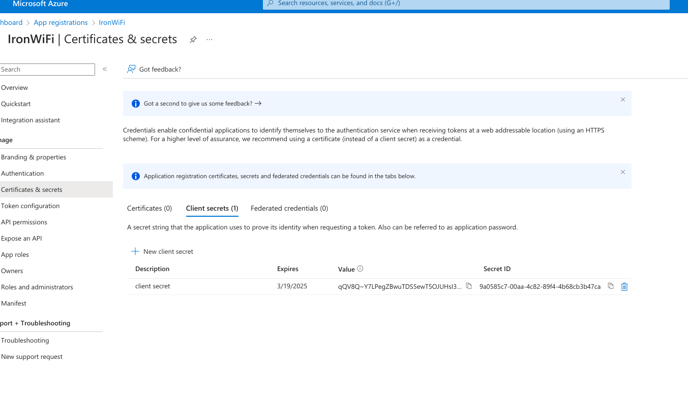
10. Now, navigate to Certificates&Secrets and create a new secret (set duration to never expires). Make sure to copy the value because you can only see it once.
IronWiFi Console
- Log in to the IronWiFi console
- Go to Users → Connectors → New Connector

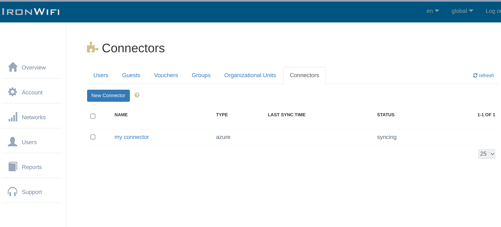
- Choose a name and pick database type - Azure AD
- Select Authentication Source: 1. Azure - will forward authentication requests to Microsoft servers for verification 2. Local will verify provided credentials locally - Cleartext-Password attribute, etc.
- Enter the Tenant identifier value (Directory ID)

- Enter the Application ID and Application Secret(Value)

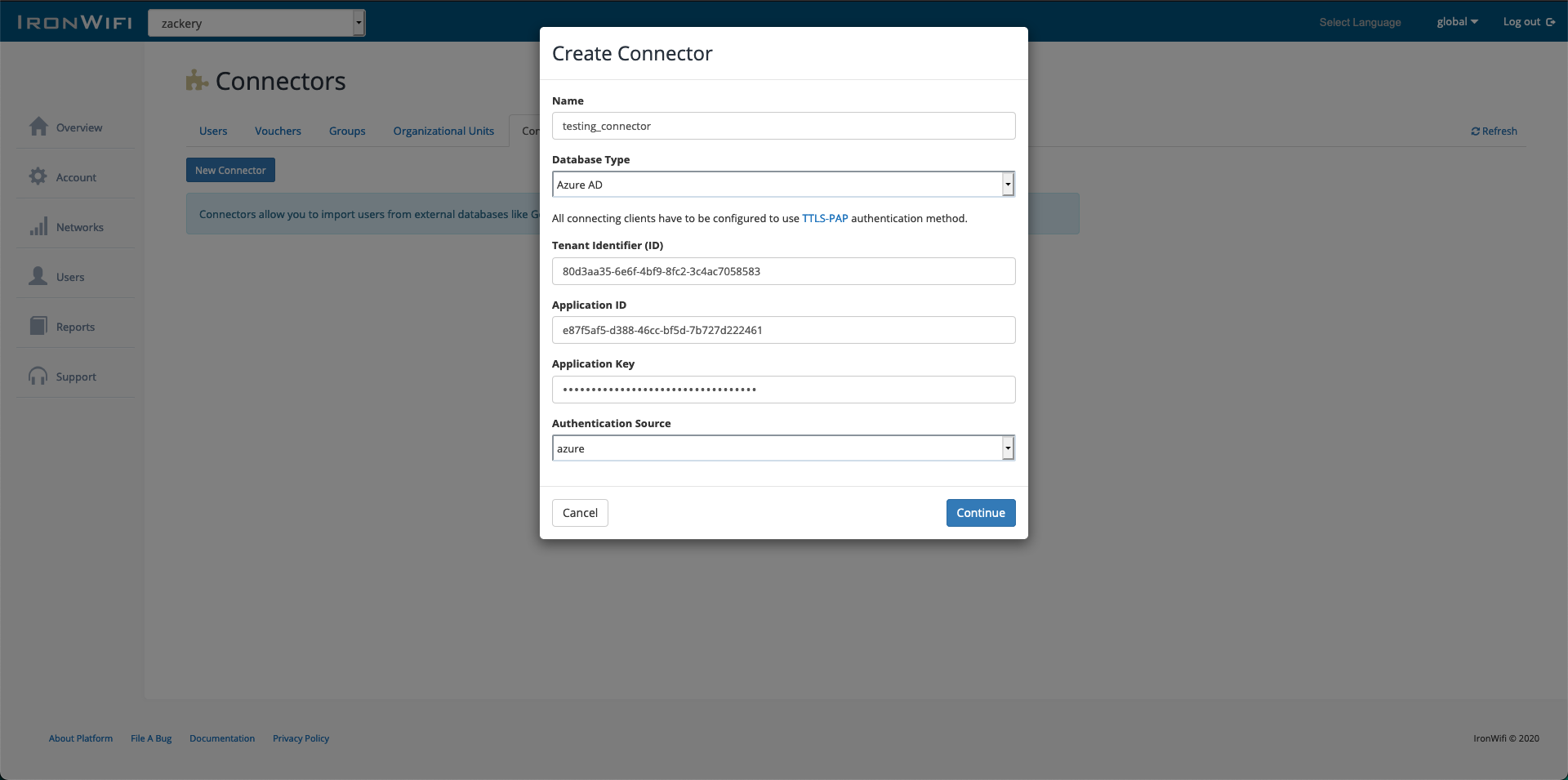
- Click the Continue button, and you will receive a unique authorization code.
- Click to Authorize, and we will redirect you to the Azure portal for authorization. Approve the request.
- Click Continue
- In the Select Group for Import window, select the Group that you want to import
Every imported user will have a random password generated. Please do not delete these generated passwords. They can be used for authentication if there is some problem with your Azure account. Deleting the generated password will disable the user's ability to authenticate.
11. Authentication
You have multiple options on how to authenticate your imported users:
Option 1: Authentication using the generated password - PEAP
During the initial synchronization, we create a random password for every imported user. Use CSV export function to export the list of passwords and provide these passwords to your users. You can also change the generated password manually or use our API.
Option 2: Authentication using certificate - TLS
You can manually create a client certificate for each user and distribute these certificates to your users. Users will be able to authenticate to your network using these certificate.
Option 3: Authentication using existing Azure account password - TTLS + PAP
If your users wish to authenticate using their existing Azure credentials, configure your clients to use the TTLS-PAP protocol.
Option 4: Authentication using existing Azure account password - PEAP-MSCHAPv2
If your users wish to authenticate using their existing Azure credentials and you have AD Domain Services enabled, create an Azure AD Bridge.
12. Configuring Client Devices
a. The easiest method is to use our profile generator tool since as you will see from the below instructions that Windows makes this setup a very cumbersome task
b. If you prefer to do it manually Follow system specific instructions on how to configure your clients:
- Windows Clients
- Android Clients
- Apple iOS, Mac OS X Clients
